How Zero Touch can supplement Zero Trust in strengthening the security of digital infrastructure deployment.
For the past years, if you were to whip a cybersecurity bingo card out in conferences, you would undoubtedly mark “blockchain,” “defense in depth,” “security by design,” and recently, “zero trust” aka ZT. Zero trust has been getting all the buzz lately for shifting defenses from traditional, network-based perimeters to focus on users, assets, and behaviors. Zero trust, as the name implies, assumes there is no implicit trust granted to users or devices.
Zero trust employs a more granular perimeter control based on identity (i.e., users), devices, geolocation, and historical usage patterns to identify whether something is to be trusted to be in the enterprise. Several ways can be put into practice to do this, from micro-segmentation and analytics to identity and access management (IAM) and multifactor authentication (MFA).
Zero trust security is a well-established concept in the security industry by now, but what’s also gradually gaining attention is zero touch security. The latter can supplement zero trust and other security efforts by automating areas that benefit from a hands-off process, like accessing sensitive data.
But are these just product marketing hype, or do they have promise?
Defining zero trust: Never trust, always verify
Since Forrester coined the term, zero trust has taken flight from a mere vision to an inescapable cybersecurity approach. According to Forrester, “Zero Trust is an information security model that denies access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices.” The architecture goes beyond approved IP addresses, ports, and protocols for validation, as was once the case with traditionally defined perimeters. Even if traffic is already inside, it is treated with zero trust.
As a result, there is stronger security that travels with the workload, even as perimeters shift, whether in the cloud, container, hybrid environment, or on-premise.
There is a caveat, though. Research firm Gartner® predicts that 60% of organizations will adopt zero-trust security by 2025 more than half, however, will fail to realize the benefits. Embracing zero trust, while “extremely powerful,” would require a cultural shift and clear communication that tie to business outcomes to be successful. After all, it’s not something like installing new security products. Like any other digital transformation, it will take a strong collaboration of partners, customers, and the industry to connect security across the ecosystem.
Defining zero touch: Security through automation
To err is human, to exploit, is threat actors’ game. When you factor people into the cybersecurity equation, the 2022 Data Breach Investigations Report (DBIR) finds that 82% of breaches result from errors in human-centric events. This finding lines up with companies looking to key security strategies that mitigate such risk.
This is where zero touch security comes in. It refers to the process wherein devices are automatically set up and configured/provisioned by an authorized user (think: admin) to automate repetitive tasks, minimize human interaction points, and reduce errors.
Sure, we humans may be equipped with certain skills that can’t be replicated by security automation, or the “machine.” At least not yet. But the machine does help in addressing issues like security skills shortage and operational inefficiencies in organizations which ultimately contribute to the security posture. Automating systems can allow incident response to identify security risks that need to be prioritized without having to check everything. Alert fatigue, anyone?
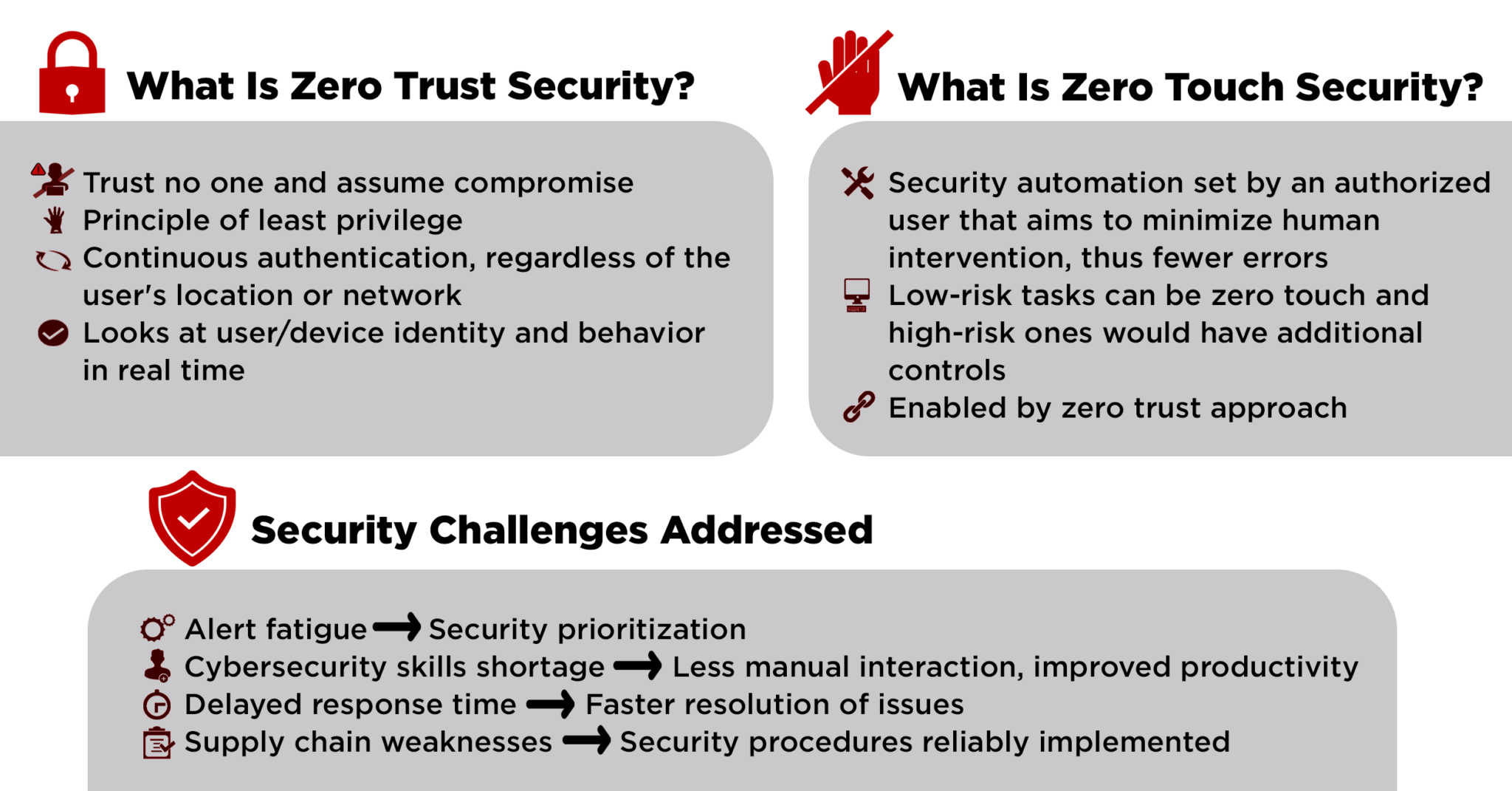
Security challenges addressed by zero trust and zero touch security
As digital infrastructures continue to evolve, access points are increasing. The security models recognize that as long as there’s inherent trust or human intervention, there is the potential for security issues. Data exposure or exploitation can occur either purposely (e.g., via an internal bad actor that causes harm to the company or an external threat actor that compromises employee credentials) or accidentally (e.g., via someone misconfiguring a setting or clicking on a phishing email).
That’s why the industry is taking notice of how a zero-trust security approach would complement technological advances and how digital businesses accelerate. Adopting a risk-based, identity-centric approach provides the needed security foundation. As security teams face the constant barrage of cyber threats, security automation is shaping up to be an answer to efficiently handling common phishing, insider risks, and other alerts.
Both zero trust and zero touch are promising as security models, and together could work well in implementing stringent measures. Well-defined models should steer a more streamlined infrastructure, better user experience, and improved security defenses, thus enabling secure digital transformation.
60%
Of organizations will adopt zero-trust security by 2025, more than half, however, will fail to realize the benefits.

